Industrial Automation & Control Systems (IACS) are an essential part of most critical infrastructure and critical services, but they are also vulnerable to cyber threats that can disrupt operations and compromise sensitive information. The term IACS refers to all the components (SCADA, PLCs, HMI etc.,) that are integrated to critical infrastructures and industrial production establishments.
Our team of cybersecurity experts has extensive experience protecting IACS networks from a range of threats, including hacking, malware, and other forms of cyber attack.
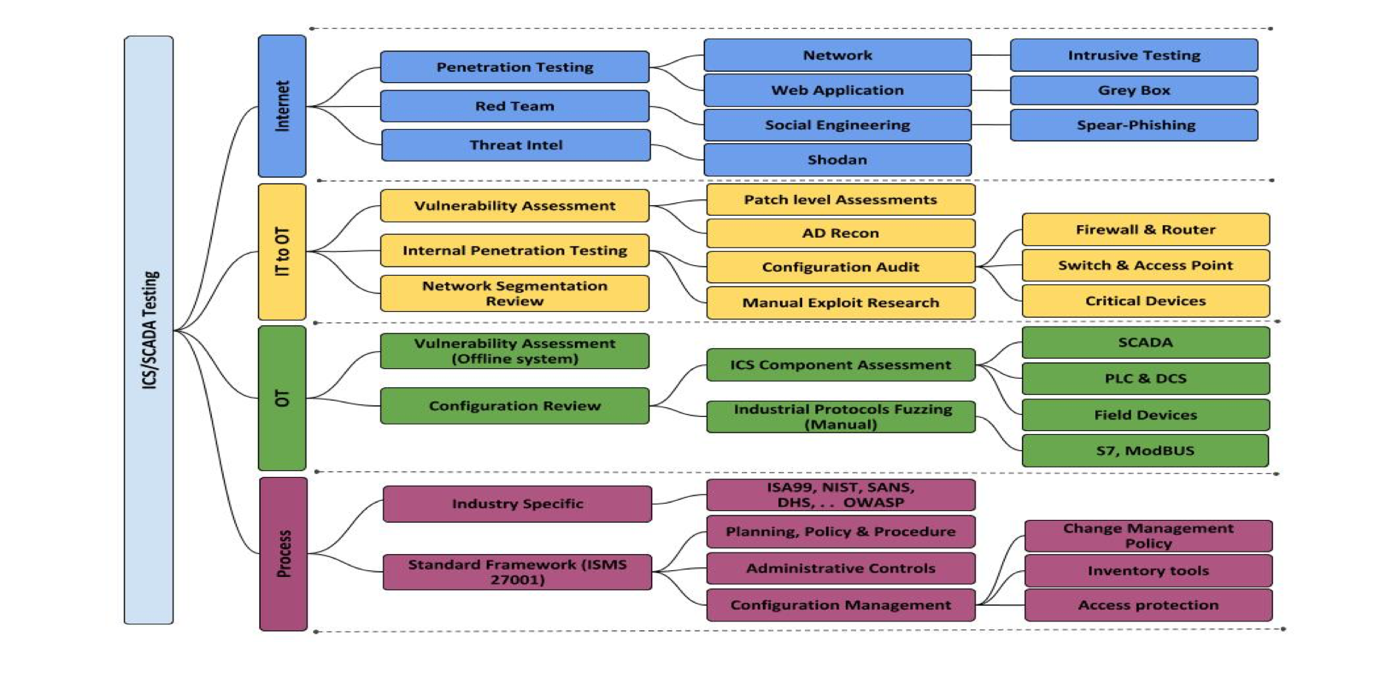
We offer a range of services to help organizations secure their IACS systems, including:
Also Read : IOT/ Embedded Systems Security
